Six
Sigma provides a set of tools and techniques for process improvement.
Eliminating defects and variation from standards in manufacturing or business
process is the basis over which Six Sigma operates on.
The success of Six Sigma was witnessed when it delivered 3.4
defects per million units or process and saved a whopping $350 million for
General Electric in 1998. Right implementation of Six Sigma is proven to yield such
results of 3.4 dpm.
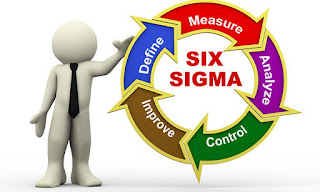
Six Sigma follows two project approaches for successful
implementation.
- DMAIC
- DMADV
DMAIC:
- Define the system, customer requirements and project goals.
- Measure key aspects of the current process and collect relevant data.
- Analyze the data to investigate and verify cause-and-effect relationships.
- Improve the current process through data analysis using techniques poka-yoke and standard work.
- Control the future state process to make sure that any deviations from the standards are corrected before they result in defects.
DMADV:
- Define design goals that are consistent with customer demands and the enterprise strategy.
- Measure and distinguish CTQs (Critical To Quality), define product capabilities, production process ability, and measure risks.
- Analyze to develop and design alternatives.
- Design a refined alternative, best suited by the analysis process in the previous step.
- Verify the design, implement the production process and hand it over to the process owner.
The successful working of Six Sigma relies not just on
training but on deep study and right implementation of the method study.
A Six Sigma training varies with the rank of employees by certifications
ranging from Green Belt, Black Belt to Master Black Belt.
Hence the implementation of Six Sigma runs all through the
organization with varied targets on every level. Skillwise Academy covers them
all with state-of-the art trainers with over 30+ years of industrial experience
in successful implementation of Six Sigma.
Our experts let your organization drive the process towards
Six Sigma and thus towards saving a huge sum of revenue every year.
Enrol yourself to the exclusive training session on Six Sigma
from Skillwise Academy.
Log on to www.skill-wise.com
for more details.